✌️How to Manage pfSense Network Gateway?
Redundant Configuration (HA) Setup Procedure
This article will introduce how to build a highly available (HA) network gateway using pfSense. This FreeBSD-based open source software will help you achieve a stable network environment.
What is pfSense?
pfSense is an open source router/firewall software based on FreeBSD that can implement various network functions such as router, firewall, VPN, and proxy. The configuration of the virtual network gateway when building ExpressRoute/Site-to-Site VPN is also described in the official documentation, so it can be used safely in many corporate environments.
File preparation
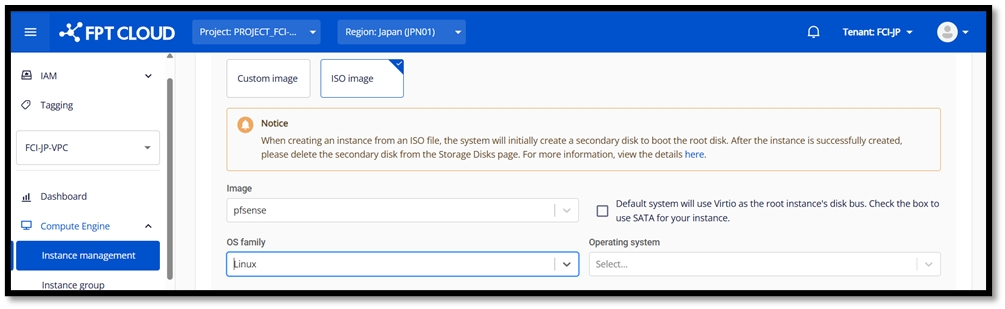
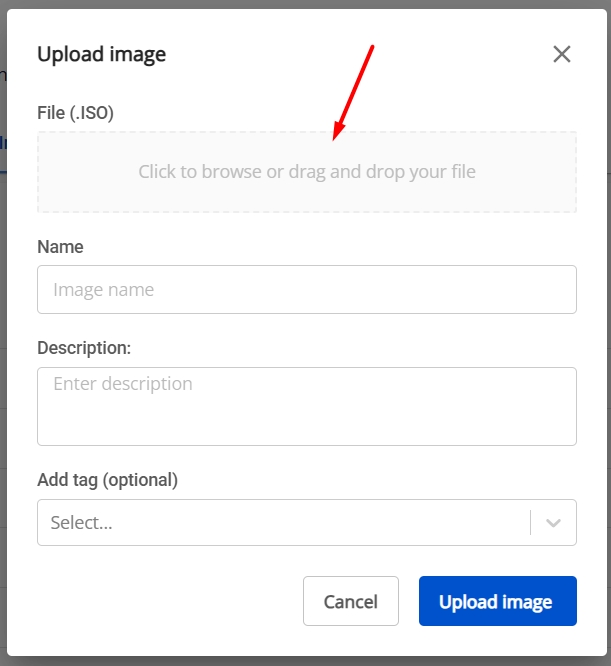
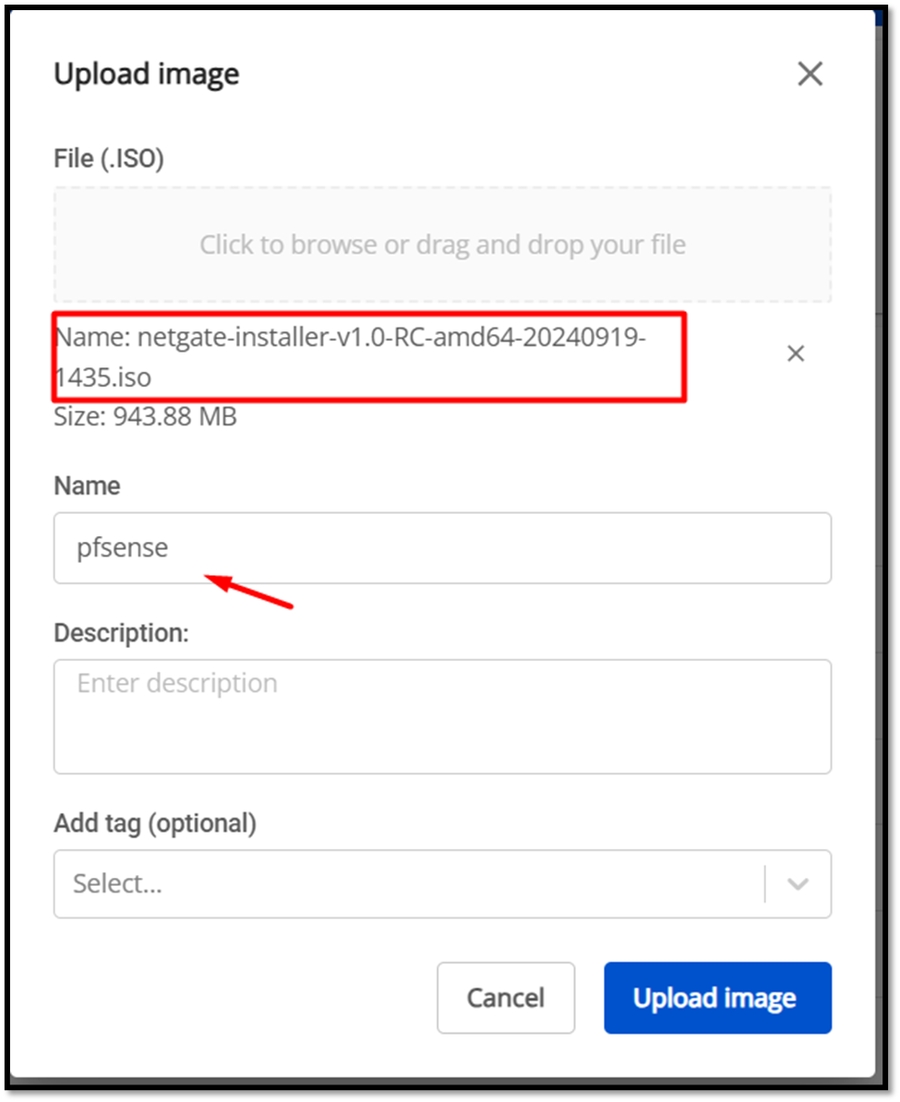
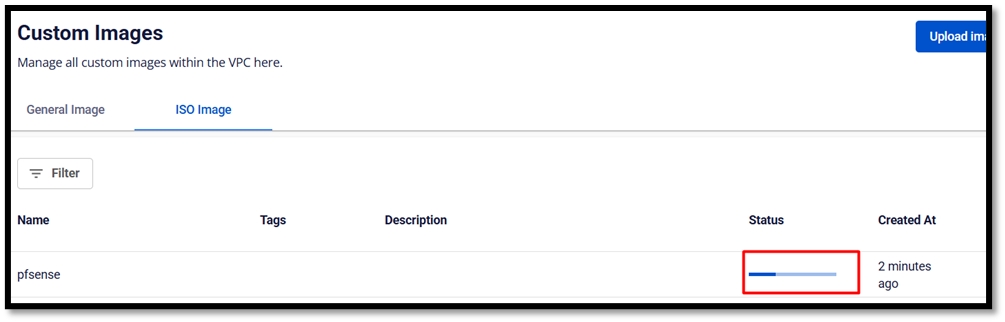
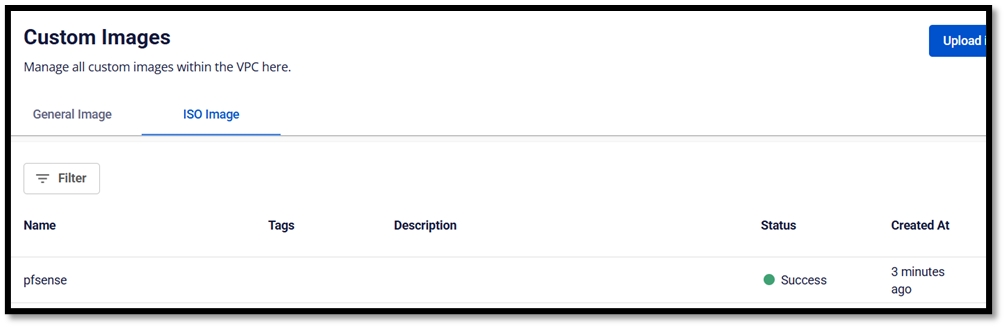
Download pfSense ISO file
Go to the official pfSense website (https://www.pfsense.org/download/) and download the latest ISO image.
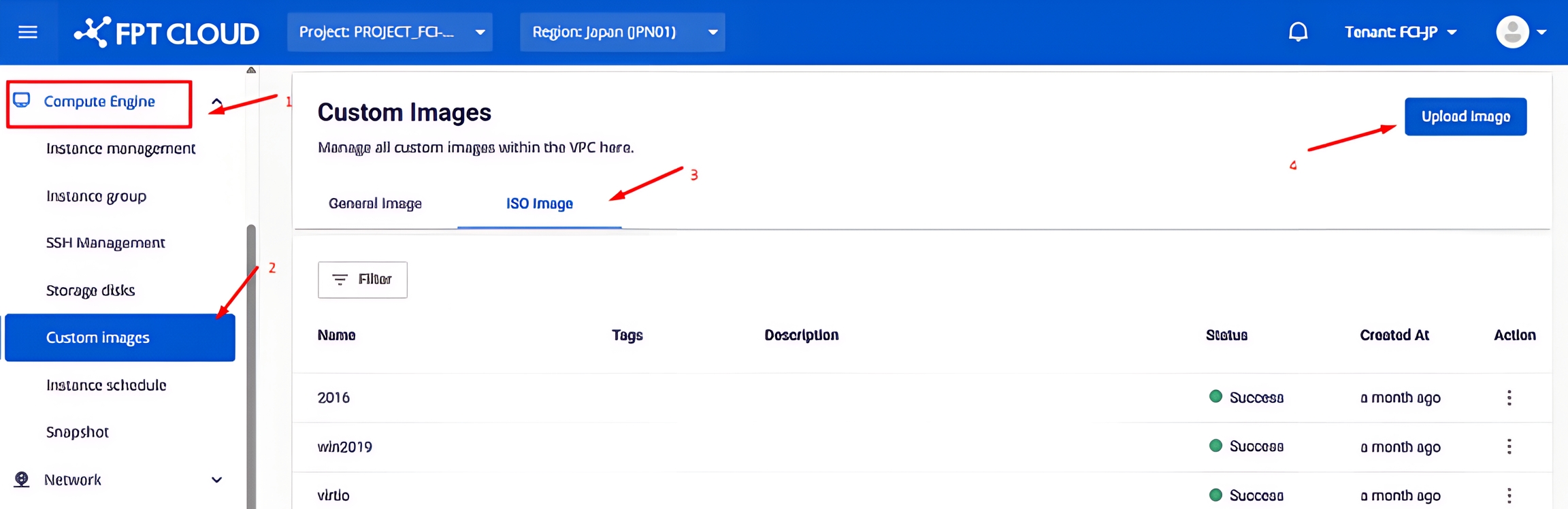
Login to FPT Cloud Console
Go to https://console.fptcloud.jp/ and log in with the provided credentials.
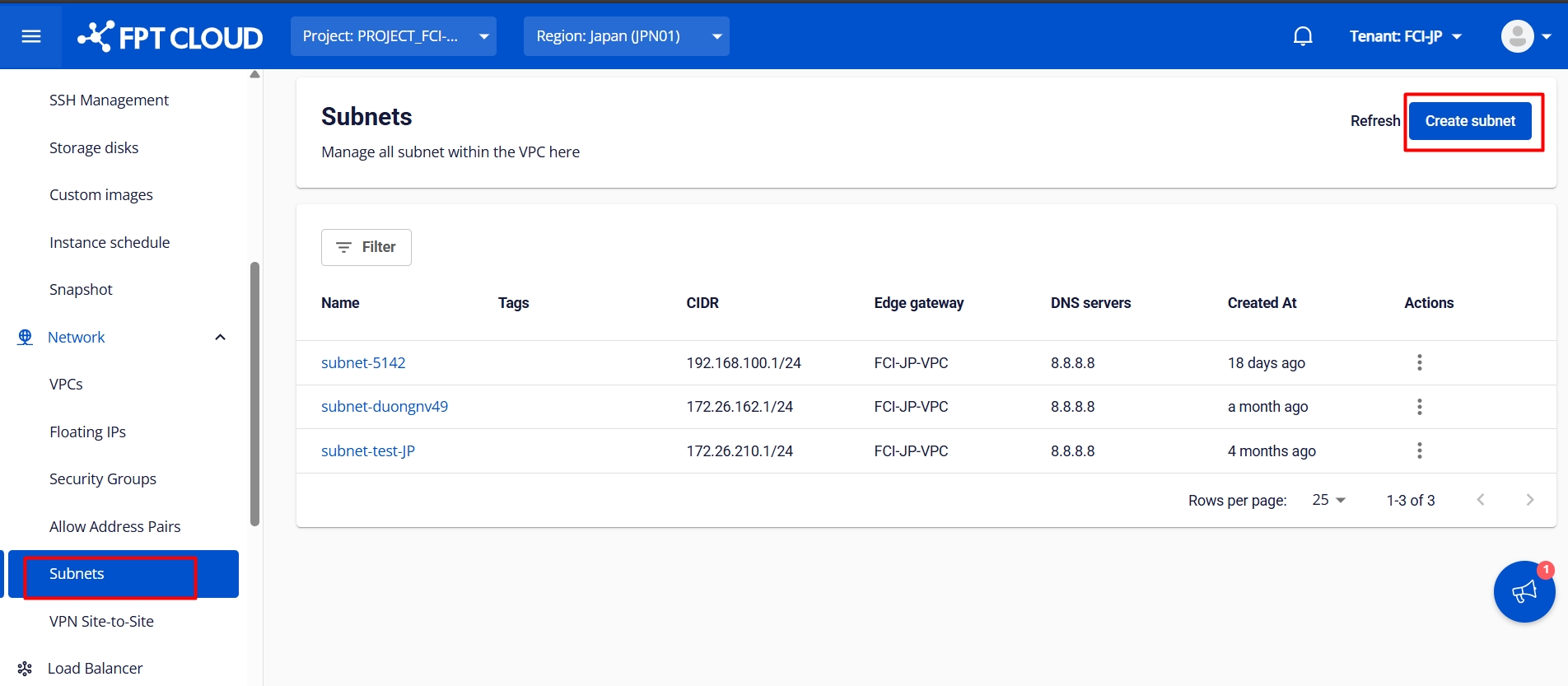
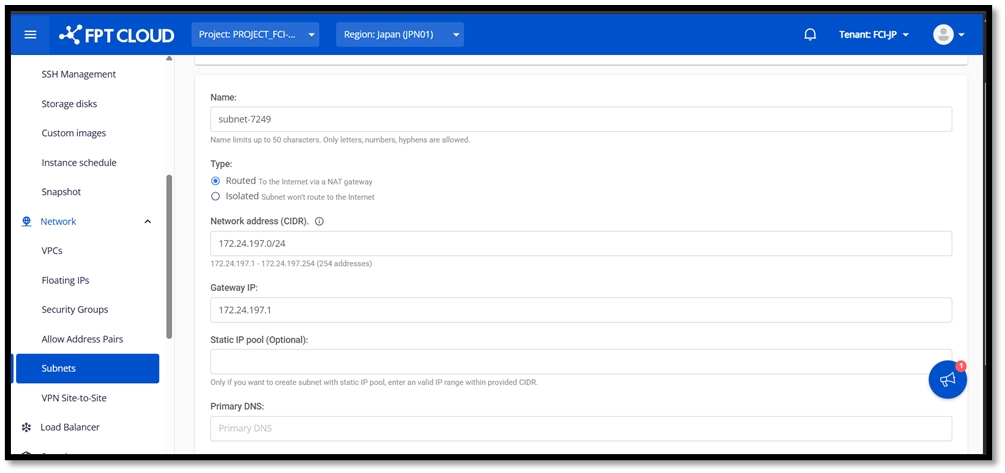
Network environment preparation
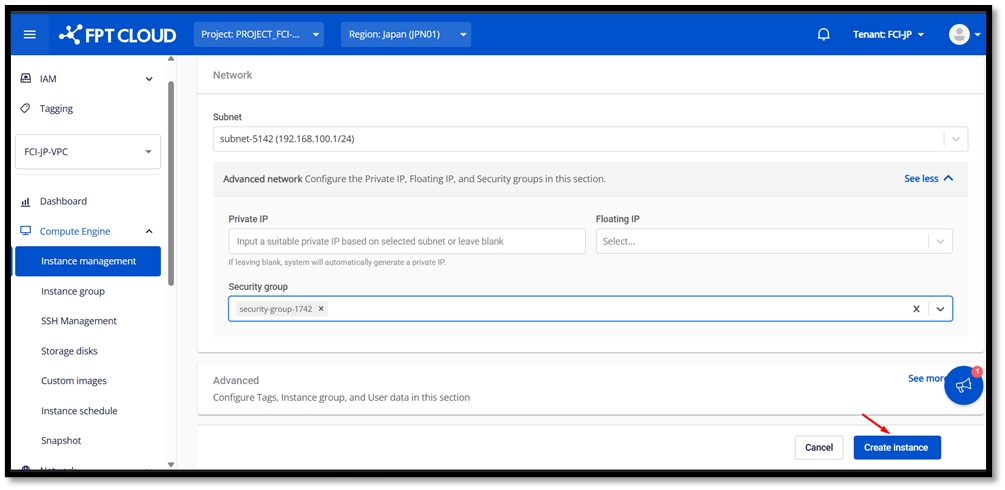
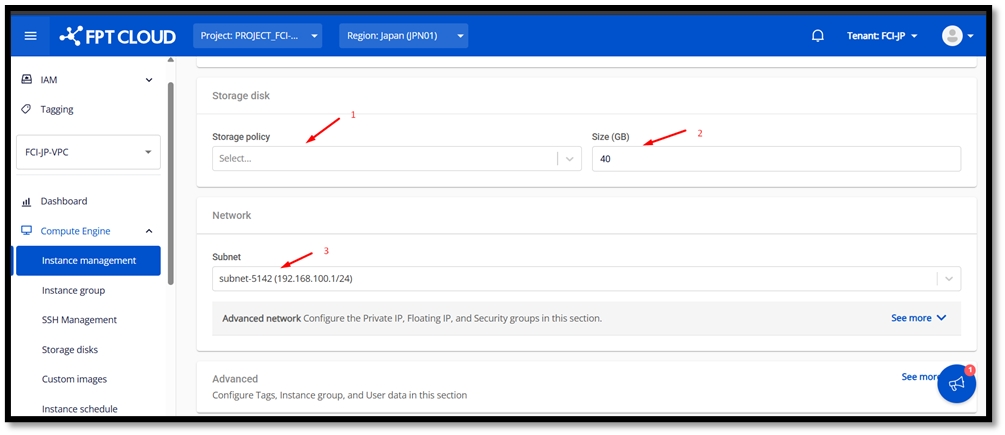
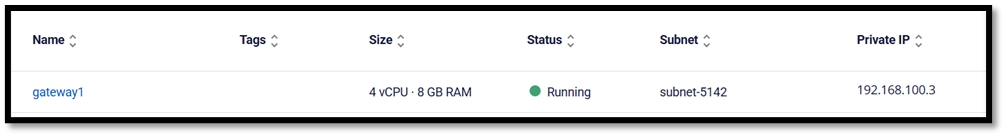
Creating a pfSense Virtual Machine
HA (High Availability) Requirements
Minimum Requirements for High Availability (HA) Implementation
At least three IPs per subnet on the pfSense network interface (one for the master, one for the slave, and a virtual IP for external communication)
Layer 2 devices must support multicast
The upstream/ISP/router involved must have access to the virtual IP used by CARP
Configuring the pfSense Interface
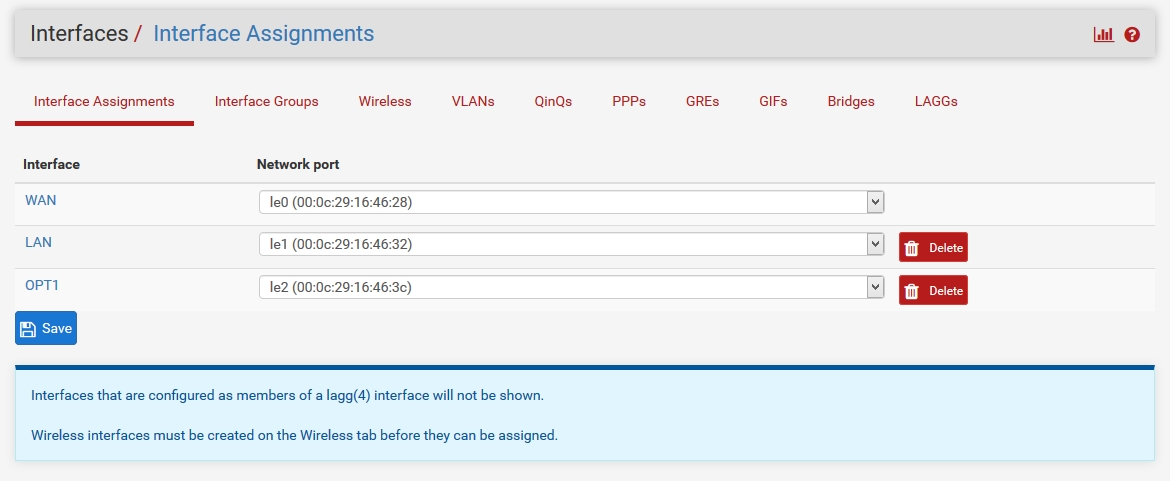
New Network: Adding a card
Select "Assignment" from the "Interface" menu and click "Add" to add a new interface.
Double-click the OPT1 interface and enter the required information.
After setting, click "Save" and then "Apply Changes".
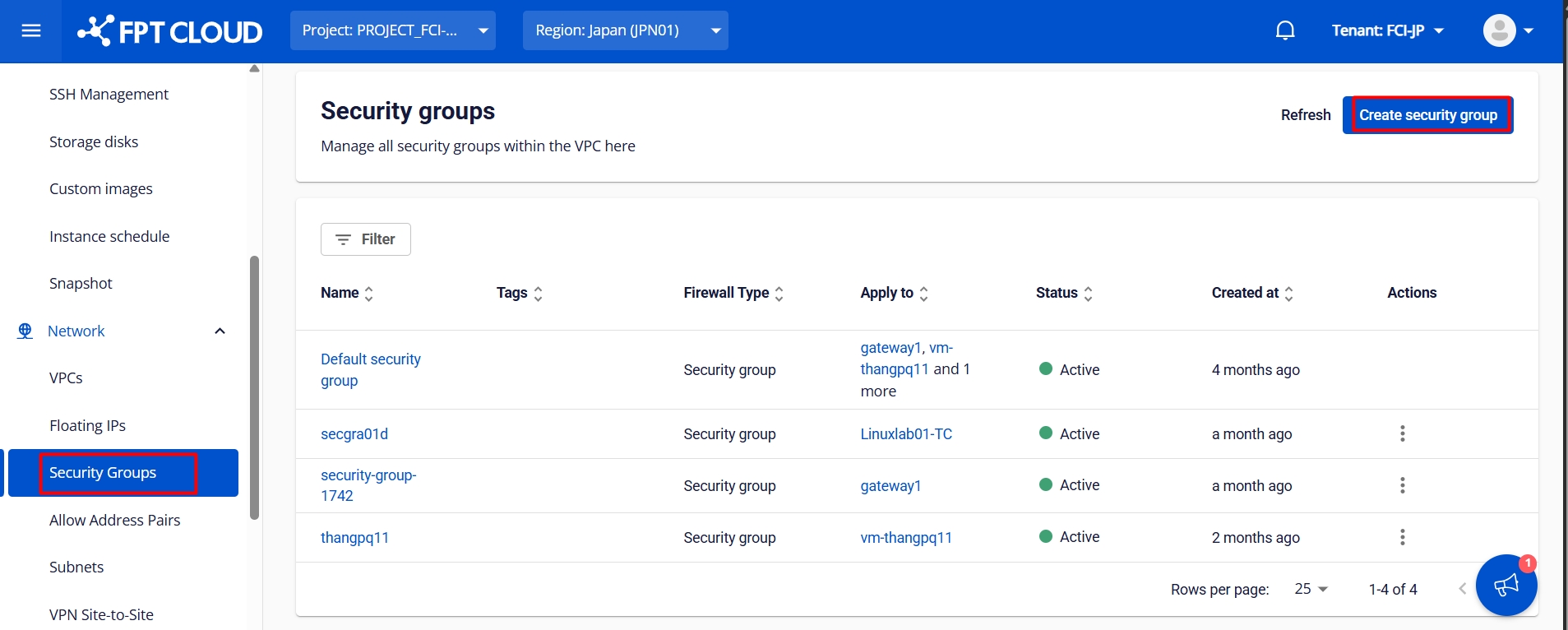
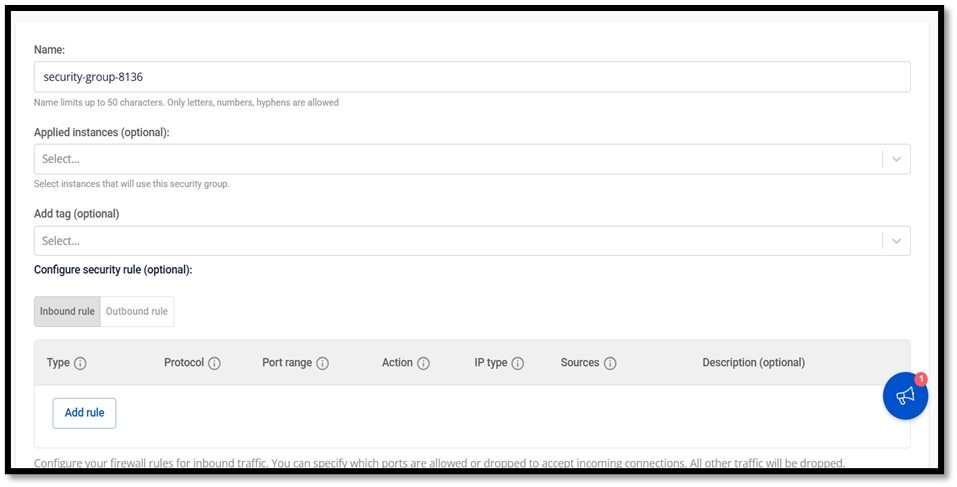
Firewall: Creating rules
Select "Rules" from the "Firewall" menu and switch to the "Sync" tab
Click "Add" to create a new rule, and enter the required information.
Once you are done with the configuration, click "Save and Apply Changes".
Do the same configuration on both pfSense servers.
Configuring CARP (High Availability Protocol)
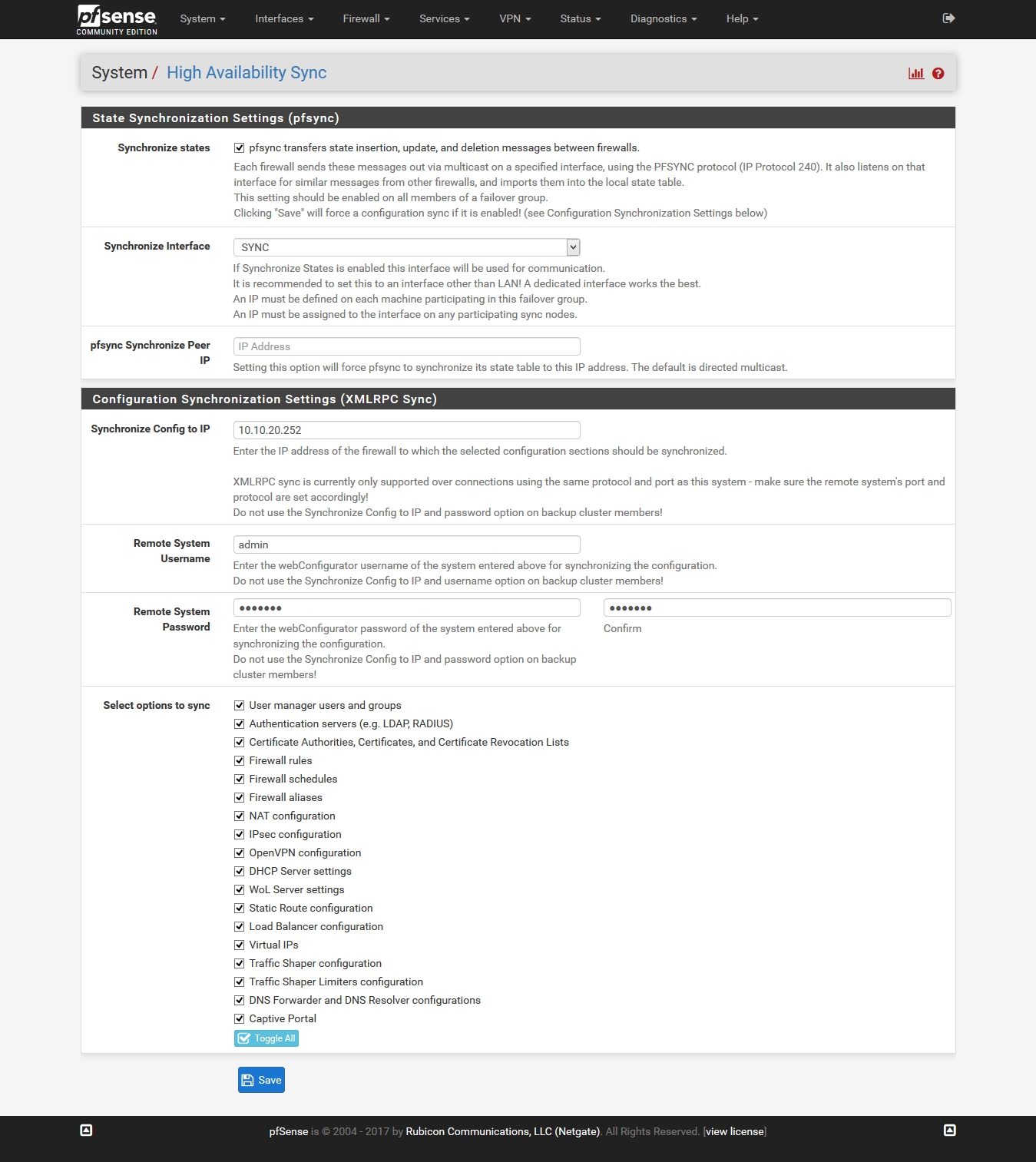
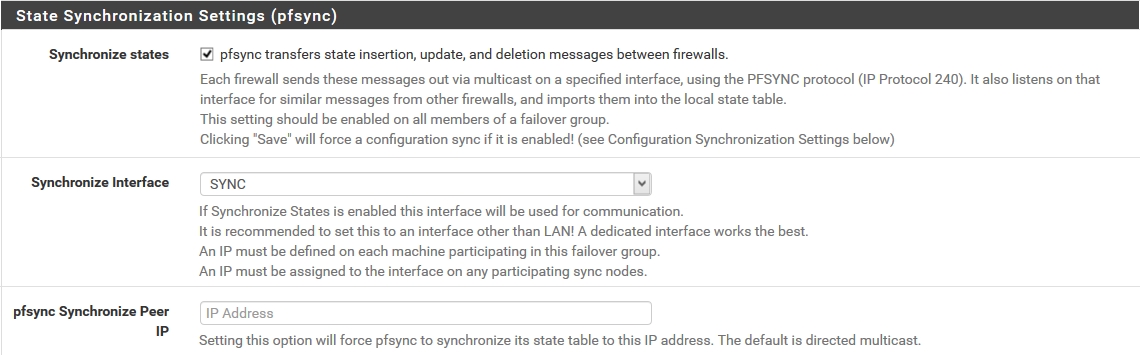
Configuring CARP on the Master
Select "High Availability Synchronization" from the "System" menu and enter the required information.
The username and password for the remote system specify the credentials of a high-privileged user on the pfSense slave virtual machine.
Configuring CARP on the Slave
Similarly, select "High Availability Synchronization" from the "System" menu and enter the required information.
The settings will be different from those of the master, so please follow the instructions to set them appropriately.
Last updated